
Why IT Asset Disposition Matters: Risks, Rewards, and Best Practices
Read More about Why IT Asset Disposition Matters: Risks, Rewards, and Best Practices

Read More about Essential Device Security Tips for Business Travelers


Read More about Why IT Asset Disposition Matters: Risks, Rewards, and Best Practices

Read More about Top 7 AV Trends Transforming Workplace Technology in 2025 So Far

Read More about Top 4 Quick Workplace Tech Upgrades That Drive Immediate Results

Read More about 5 Quick Safety Tips from Construction Safety Week 2025

Read More about 6 Reasons Why Businesses Need Cyber Security Awareness Training: The 2025 Edition

Read More about What’s New with Copilot Agents: The Latest Enhancements You Should Know About

Read More about Copilot in Teams and Outlook: Updates That Transform Your Workday


Read More about Copilot in Word: From Blank Page to Polished Documents in Minutes

Read More about PowerPoint Transformed: Latest Copilot Features That Streamline Presentation Creation

Read More about Copilot Chat Updates: 6 New Features That Matter

Read More about Essential Device Security Tips for Business Travelers

Read More about Managed Services Newsletter: Empowering Client Success through Excellence in Service

Read More about Align Insights: Experts React to the SEC's Cyber Crackdown

Read More about Migrations Newsletter: Discover Align's Migration Solutions: Videos, Thought Leadership, and More!

Read More about What Business Leaders Need to Know About Wi-Fi 6E and 7 in 2025

Read More about Why Your Wireless Network Needs a Safety Net: A Guide to Wi-Fi 6E and Wi-Fi 7 Redundancy

Read More about The Hidden Value of Data Center Inventory: Lessons from the Field

Read More about 6 Workplace Technology Trends Shaping the Future of Work in 2025

Read More about 5 Critical Data Center Trends Reshaping the Industry in 2025

Read More about Top 2025 Technology Innovations Transforming the Alternative Financial Services Space

Read More about Quick Q & A with Three Liquid Cooling Experts

Read More about InfiniBand Series - Part 4: How InfiniBand and AI are Dramatically Reshaping Data Center Infrastructure

Read More about Quick Tips for Safe Online Shopping this Holiday Season

Read More about Drowning in Data Center Inventory? Here's your Lifeline.

Read More about 5 Benefits of Outsourcing IT with a Managed Service Provider in 2025

Read More about 5 Ways to Reduce the Risk of Cyber Attacks

Read More about From the Experts: What you Need to Know About Building a Data Center in New Jersey

Read More about Real Talk with Align’s CEO, Jim Dooling: Navigating the Future of Data Center Infrastructure

Read More about Event Recap: Advancing Data Center Design Engineering

Read More about Navigating Office Internet Choices: A Guide for Business Leaders


Read More about The Rundown of New Jersey’s New AI Infrastructure Tax Credit Program

Read More about IT Due Diligence Checklist for Evaluating Managed Service Providers

Read More about Empowering Client Success through Excellence in Service

Read More about Key Takeaways from WORKTECH Events in London & New York
Read More about Get to Know Align's 2024 Summer Interns!

Read More about InfiniBand Series - Part 3: Building a Network for High-Performance Computing and AI

Read More about Financial Firms Return to Office: Is Your Workplace Ready?

Read More about The 6 Types of Virtual Migration Strategies and How to Pick the Right One

Read More about Data Center Update: Growth, Success Stories, and Industry Insights

Read More about Align Insights: Industry Leaders Discuss Enhancements to Regulation S-P

Read More about InfiniBand Series - Part 2: A Closer Look at Cables, Termination Types, and Fiber Innovations

Read More about Verkada's Hybrid Cloud Storage: A Breakthrough in Video Surveillance Technology

Read More about InfiniBand Series - Part 1: Demystifying the InfiniBand Versus Ethernet Debate

Read More about The Introduction of the Chief Workplace Officer is Proof that a Collaborative Workplace is Fundamental
Read More about Microsoft Copilot: Your assistant for solving complex work problems.

Read More about Copilot in Excel: Identify trends. Create powerful visualizations. With ease.
Read More about Copilot in Word: Get writing faster. Summarize in seconds.
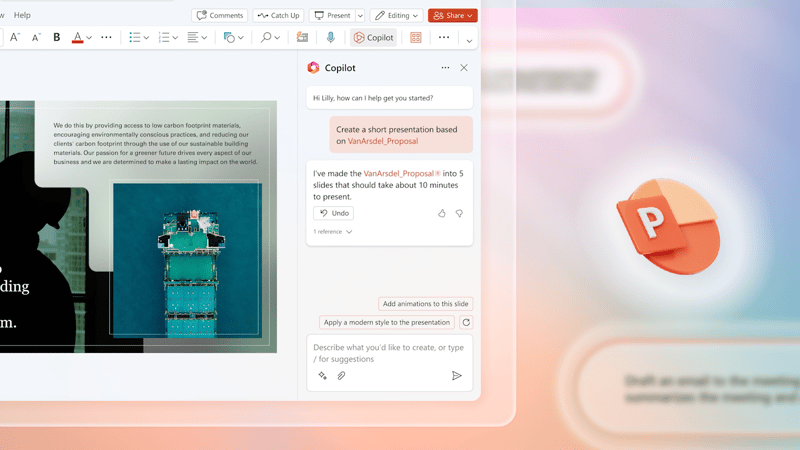
Read More about Copilot in Powerpoint: Turn your ideas into stunning presentations, simply.
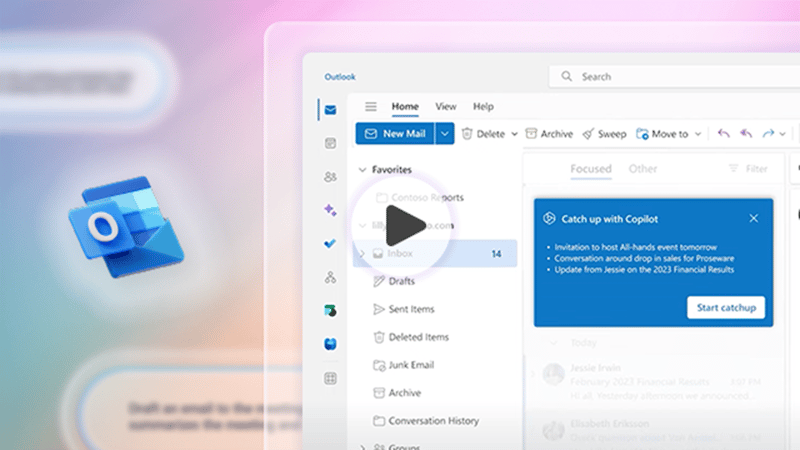
Read More about Copilot in Outlook: Reduce inbox stress. Improve email efficiency.
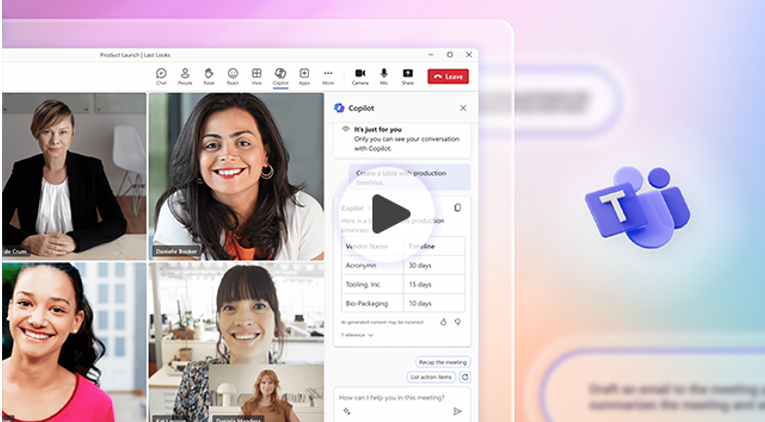
Read More about Mastering your Meetings: How Copilot Takes Teams to the Next Level

Read More about Align's Guide to Effortless Efficiency with Copilot

Read More about Navigating the AI frontier: Balancing data center evolution with AI revolution
Read More about Providing a flexible, secure, cost-effective, and unified cloud experience

Read More about Align Named Top 10 Data Migration Company to Watch in CIO Coverage

Read More about Empowering the Data Center: Recent Projects, Tech Solutions, and Trends Unveiled!

Read More about The Rising Need for IT Asset Disposition Services in a Data-Driven World

Read More about 5 Essential Elements to Designing Conference Rooms Built for the Hybrid Professional

Read More about Cybersecurity Education 101: No Time for Ignorance

Read More about The MGM Wake-Up Call: Hackers Breach Casino Giant MGM Grand


Read More about Sharing with Caution - Social Media Security Tips

Read More about 4 Crucial Design Considerations When Building Your Office's Multipurpose Room

Read More about How Secure is Your Password? (Hint: It's Not as Strong as You Think)

Read More about What You Should Look for in a Project Manager – Before the Project Kicks Off

Read More about The Evolution of Wi-Fi Continues: The Next Generation

Read More about 6 Hot Products for the Modern Workplace Discovered at ISE 2023

Read More about Industry Experts Weigh In On 2023 SEC Examination Priorities

Read More about 7 Smart Building & Collaboration Technologies that Enable the Hybrid Professional

Read More about The Dangers of Aging IT Infrastructure

Read More about The Office, Reimagined: Top Trends Shaping the Workplace in 2023

Read More about Global Data Center Trends & 2023 Predictions

Read More about Tools to Tackle Diverse Security Challenges

Read More about DAS and Small Cell in London: Can You Hear Me Now?

Read More about Investment Advisor Cybersecurity: 16 Must-Know Recommendations

Read More about Understanding Cybersecurity Risk Posture: What is it and why do I need it?

Read More about Hackers Drain $570 Million from World's Largest Cryptocurrency Exchange

Read More about Fiduciaries and Cybersecurity Professionals Beware: Managing Cybersecurity Risk Can Lead to Criminal Liability for Individuals

Read More about Align Data Center and Migrations Team Updates

Read More about 4 Reasons to Move to the Public Cloud

Read More about The Biggest Regulatory Factors Affecting Cybersecurity Budgets
Read More about What's Hot in AV: Takeaways from InfoComm 2022

Read More about Align COO Vinod Paul Featured on Cavelo Insider

Read More about Going Green: The Path to Data Center Efficiency and Sustainability

Read More about Important Network Considerations When Migrating to the Cloud

Read More about Align Featured in 2022 US Hedge Fund Start-Up Guide by Hedgeweek

Read More about Creating Your Data Migration Roadmap

Read More about The Hybrid Workplace: Keeping Employees Connected In and Out of Office

Read More about Reduce Cyber Risk with Align's Data Discovery & Protection Platform, Powered by Cavelo

Read More about How to Bolster your Cybersecurity Response Amid Tensions Between Russia and Ukraine

Read More about SEC Release: Proposed Rules on Cybersecurity

Read More about The Log4j Vulnerability and its Impact on the World of Security

Read More about Align Featured in Hedgeweek Report: Best Cybersecurity Provider
Read More about Traveling for the Holidays? Here are 7 Cybersecurity Best Practices

Read More about 10 Technologies for Supporting the Hybrid Office

Read More about Benefits of Data Center Consolidation


Read More about CYBER ALERT: A Zero-Day, Zero-Click Exploit Infecting Apple Devices.

Read More about CYBER ALERT: SEC Charges Firms with Deficient Cybersecurity Procedures

Read More about Three Benefits to Performing a Workload Assessment

Read More about Don’t Forget These 5 Steps Before Migrating to the Cloud

Read More about CYBER ALERT: Kaseya VSA Supply-Chain Ransomware Attack

Read More about Four Global Enterprise Data Center Transformations

Read More about How to Accelerate Digital Transformation

Read More about LORCA Cyber Workshop: Securing Today's Hybrid Infrastructure

Read More about The Unforeseen Challenges of Remote Work: Hardening Your Home Network
Read More about SEC Announces 2021 Examination Priorities

Read More about What's the Difference Between Private, Public, Colocation and Hybrid Cloud?

Read More about The Benefits of Digital Transformation

Read More about The 2020 Investment Adviser Adaptation



Read More about Hedgeweek Award: Align Named Best Cloud Services Provider

Read More about Why Use Serialized Labeling in Your Data Center
Read More about 5 Signs You Need to Improve Risk Management

Read More about Ongoing Phishing Scam Impersonating FINRA

Read More about SEC Issues Cybersecurity Risk Alert on Compromised Credentials

Read More about Data Centers in the Age of COVID-19

Read More about Common Phishing Attack Methods and Tips to Avoid Scams


Read More about Successfully Migrating IT During COVID-19
Read More about SEC Risk Alert: COVID-19 Compliance Risks for Broker-Dealers and RIAs


Read More about SEC Risk Alert Urges Investment Industry to Strengthen Cybersecurity


Read More about Fundamentals of Vulnerability Management

Read More about Investment Managers Adapt for Post-Covid-19 World: Part 2

Read More about Technology, IT and Cyber Tips Post-Covid-19: Part 1

Read More about Hackers Seize $10 Million from Sovereign Wealth Fund

Read More about Remote Work Raises Cybersecurity, Complacency Fears for Hedge Funds

Read More about 4 Ways COVID-19 Has Forever Altered Business as Usual

Read More about Heightened Hedge Fund Regulation: IT, Cybersecurity and Preparation

Read More about How to Protect Your Business from Coronavirus Phishing & Cyber Scams
Read More about Coronavirus Business Continuity and Preparedness

Read More about Scam Alert: Criminals Cloning Hedge Fund Websites

Read More about 2020: 7th Consecutive Year SEC Declares Cybersecurity as Top Regulatory Priority


Read More about Next-Gen Managed Services Fueled by Public Cloud Innovation

Read More about New Corporate Phishing Scam Mimics Employee Evaluations


Read More about Data Center Inventory is More Important than Ever

Read More about Own Your Own Data Center? 4 Questions You Need to Ask Yourself Before Deciding to Consolidate and How to Win in the Short Term

Read More about Why the ITS Cabling Expert Is Your Critical “Translator” Through All Phases of the Building Process

Read More about Top Five Data Center Cable Connectivity Issues

Read More about How Fund Managers Can Prepare for the Latest SEC OCIE Cyber Sweeps



Read More about How to Improve Your Organization's Culture Through Technology

Read More about From Hedge Fund to FinTech – Is the Grass Greener on the Other Side?

Read More about A "Hot Spot" You Want to Avoid: How to Use Data Center Containment

Read More about Advantages of IT Outsourcing Services

Read More about Best Practices to Design and Manage Your Organization’s WiFi

Read More about (VIDEO) Align's Application Migrations Portal

Read More about How IoT Will Transform Office Space Utilization

Read More about 6 Signs You Need to Change Your IT Managed Service Provider

Read More about Tips for Reducing IT Spend During an Office Fit Out
Read More about Expert Cyber Security Tips to Stay Safe This Memorial Day Weekend

Read More about 4 Reasons to Invest in ITS Infrastructure Design and Build

Read More about Verizon DBIR: Key Findings and Recommendations for your Business

Read More about Building Authentic Client Relationships in the Data Center World

Read More about Align to Sponsor 2019 SALT Conference with eSentire

Read More about Hacking Techniques, Breach Effects and Prevention Tips


Read More about Mobile Device Management: What You Need to Know

Read More about Is Your Data Center Design and Build Provider Highly Engaged?

Read More about Top Cyber Threats and Security Tips for Hedge Funds
Read More about Change or Perish: The evolving demands of the modern Managed IT Service Provider

Read More about SEC OCIE to Launch a Third Cybersecurity Sweep
Read More about 8 Due Diligence Questions to Ask Public Cloud Service Providers

Read More about Top 5 Trends From 2019's Data Center World Expo

Read More about Fund Managers Embrace Public Cloud to Boost Cybersecurity, Efficiency

Read More about Top Real Estate Trends for Building a Digital Workplace

Read More about Five Signs Your Business is Using a Legacy Cloud Solution

Read More about Why Should Hedge Funds Embrace the Public Cloud?

Read More about (PODCAST) A Closer Look at Cybersecurity Practices

Read More about Top IT Infrastructure Trends in 2019

Read More about The Benefits of Office 365 Migration


Read More about Can Your Team Be Tricked by CEO Fraud?

Read More about Risk Management Solutions for Hedge Funds

Read More about 2018 Data Breach Recap: 8 Significant Incidents

Read More about Forwarding-Thinking Investment Firms are Embracing Public Cloud Benefits


Read More about Digital Transformation with Managed IT Providers

Read More about The Growing Dangers of Ransomware

Read More about Top 4 Cyber Security Tips for Growing Hedge Fund Startups

Read More about Align Named Top 10 Data Center Services Company By CIO Applications

Read More about Cybercriminal Profits Soar from Business Email Compromise (BEC) Scams

Read More about 2019 IT Trends Outlook: Digital Transformation, Outsourcing IT and More

Read More about Five Ways to Develop a Cybersecurity Culture

Read More about Pioneering Cybersecurity Advisory Services: Hedgeweek Special Report

Read More about Market Leading Solutions in an Evolving Digital Landscape (Part 2)

Read More about Market Leading Solutions in an Evolving Digital Landscape (Part 1)

Read More about Three Tips for Balancing Data Center Power

Read More about Why Cybersecurity Needs a New Approach

Read More about National Cybersecurity Awareness Month: How Security Training Can Benefit Your Business