The following article was written by Chris Mihm, Director of Managed Cloud Services at Align, as part of Align’s National Cyber  Security Awareness Month (NCSAM) Article Series.
Security Awareness Month (NCSAM) Article Series.

Photo Credit: © kras99 - stock.adobe.com
If you missed Tuesday’s article, read Something Seems “Phishy” – How to Identify and Avoid Phishing Scams here.
Microsoft Azure makes it simple to deploy IaaS resources in the public cloud. As a result, it can become easy to forget, or even bypass, best practices for securing your Azure IaaS resources. The following is a list of common best practices that may be utilized when deploying Azure resources via the Azure Resource Manager (ARM) portal. Specific use cases will ultimately dictate deviation when necessary, but for most deployments, these hold up.
Virtual Private Network
Creating a Site-to-Site (S2S) VPN connection between your on-premises network and your Virtual Private Network in Azure provides a secure, dedicated, IPsec tunnel for communicating. With a Site-to-Site VPN connection in place, you can completely remove specified public access and simply connect via the internal ports as you would with any other machine on your internal network. Another option is to create a Point-to-Site (P2S) VPN connection, which establishes a secure connection directly from a computer to the Virtual Network without having to acquire and configure a VPN device, as would be necessary for a Site-to-Site VPN connection. Both S2S and P2s are great ways to reduce external threats by removing the public facing access. See Create a Site-to-Site connection in the Azure portal for setting up and configuring a S2P VPN connection. Additionally, see Configure a Point-to-Site connection to configure a P2S VPN connection.
ExpressRoUTE
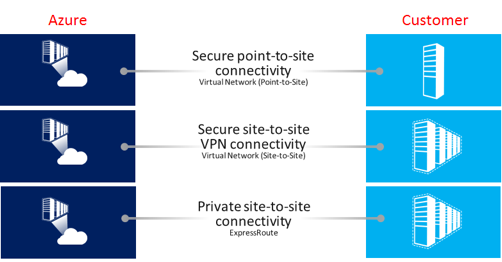
ExpressRoute creates private connections between Azure datacenters and either on premises infrastructure or in a co-location  environment. ExpressRoute connections are not transmitted over the public Internet, and offer greater reliability, faster speeds, lower latencies and higher security than typical connections over the Internet. With ExpressRoute, you can establish connections to Azure at an ExpressRoute location or directly connect to Azure from your existing WAN network provided by a network service provider.
environment. ExpressRoute connections are not transmitted over the public Internet, and offer greater reliability, faster speeds, lower latencies and higher security than typical connections over the Internet. With ExpressRoute, you can establish connections to Azure at an ExpressRoute location or directly connect to Azure from your existing WAN network provided by a network service provider.
Secure Endpoints with Network Security Groups (NSGs)
A network security group (NSG) contains a list of security rules that allow or deny network traffic to resources connected to Azure Virtual Networks (VNet). NSGs can be associated to subnets and individual network interfaces attached to VMs (Resource Manager). When you deploy a virtual machine, a default NSG is created with 1 inbound security rule to allow VM management. The VM is initially be configured with a public IP. It is recommended to dissociate the public IP from the Azure Arm portal in order to remove public facing access to the VM. This is a great way to reduce external threats.
Usernames, Passwords and Multi-factor Authentication
When provisioning and accessing resources in Azure, users are required to authenticate. Enforce complex usernames and
passwords for your VMs. Azure requires passwords to be between 12 and 123 characters long and must contain 3 of the following: a lowercase character, an uppercase character, a number and a special character. In addition to strong passwords, it is good practice to enforce multi-factor authentication which adds a second layer of security to user sign-ins. This reduces the likelihood that compromised credentials will have access to an organization’s data.
Manage your VM security posture with Azure Security Center
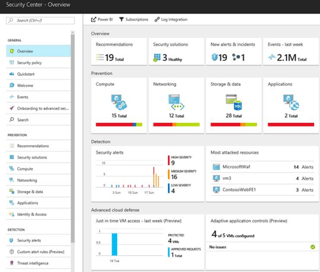
Azure Security Center provides unified security management and advanced threat protection for workloads running in Azure, on-premises, and in other clouds. It delivers visibility and control over hybrid cloud workloads, active defenses that reduce your exposure to threats, and intelligent detection to help you keep pace with rapidly evolving cyberattacks with active threat monitoring and security alters.

Security Center is offered in two tiers:
- The Free tier is automatically enabled on all Azure subscriptions, and provides security policies, continuous security assessment, and actionable security recommendations to help you protect your Azure resources.
- The Standard tier extends the capabilities of the Free tier to workloads running in private and other public clouds, providing unified security management and threat protection across your hybrid cloud workloads. The Standard tier provides advanced threat detection capabilities.
For more information on Azure Security center, see Introduction to Azure Security Center.
Protect data at rest in VMs by enforcing encryption
For many organizations, data encryption at rest is a mandatory step towards data privacy, compliance and data sovereignty. Azure Disk Encryption enables IT administrators to encrypt Windows and Linux IaaS Virtual Machine disks. Azure Disk Encryption protects and safeguards data to meet organizational security and compliance requirements. Encryption mitigates risks related to unauthorized data access. Organizations that do not enforce data encryption are more likely to be exposed to data integrity issues, such as malicious or rogue users stealing data and compromised accounts gaining unauthorized access to unencrypted data. For more info visit, Azure Data Security and Encryption Best Practices.
In addition to the above recommendations, there are other numerous methods that are available to secure Azure IaaS resources. Documentation on these resources can which can be found at Microsoft. Further information regarding Align’s cloud services offerings can be found here.
Documentation on these resources can which can be found at Microsoft. Further information regarding Align’s cloud services offerings can be found here.For more information about our services, contact info@align.com or visit: www.aligncybersecurity.com and www.align.com.
Come back next Tuesday for our next article in our National Cyber Security Awareness Month (NCSAM) Series!

About the Author
Chris is an IT professional with over 19 years of experience in customer facing roles including designing, architecting and managing the implementation of cloud solutions, information systems and technologies for small to mid-size companies. He has a broad range of skills and knowledge around virtualization and cloud technologies.
Images courtesy of Microsoft: VPN Security Center



