
Photo Credit: © turbomotion046 - stock.adobe.com
Often the worst cyber-crimes start with a simple slip-up: opening an email and falling prey to a phishing attack. All too often, we see entire companies in the grips of ransomware over a single error from a lapse in diligence, incurring significant losses and downtime that were otherwise preventable.
More malicious emails are making their way to your inbox than ever before. Email phishing attacks remain a popular method of infiltrating devices and stealing credentials. As attackers grow more persistent and resourceful, consumers and employees must remain vigilant against security threats. It’s likely that we’ve all seen emails that seem to have come out of nowhere but otherwise look authentic, but is that innocuous-looking truly email safe? Here’s a quick quiz to test your ability to spot the signs of an unsecured or dangerous email. When you’re done, scroll down to view the highlighted solutions:
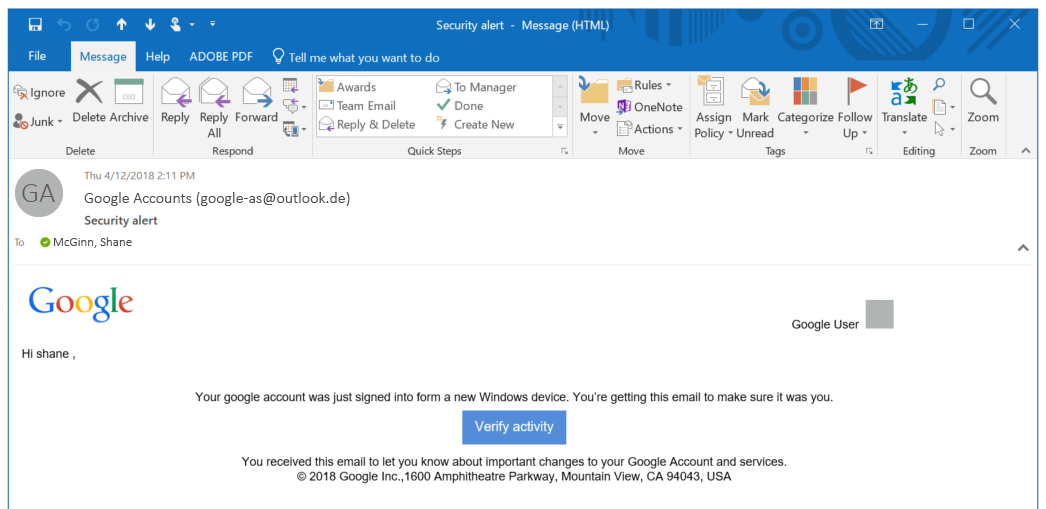
Were you able to spot all of the red flags?
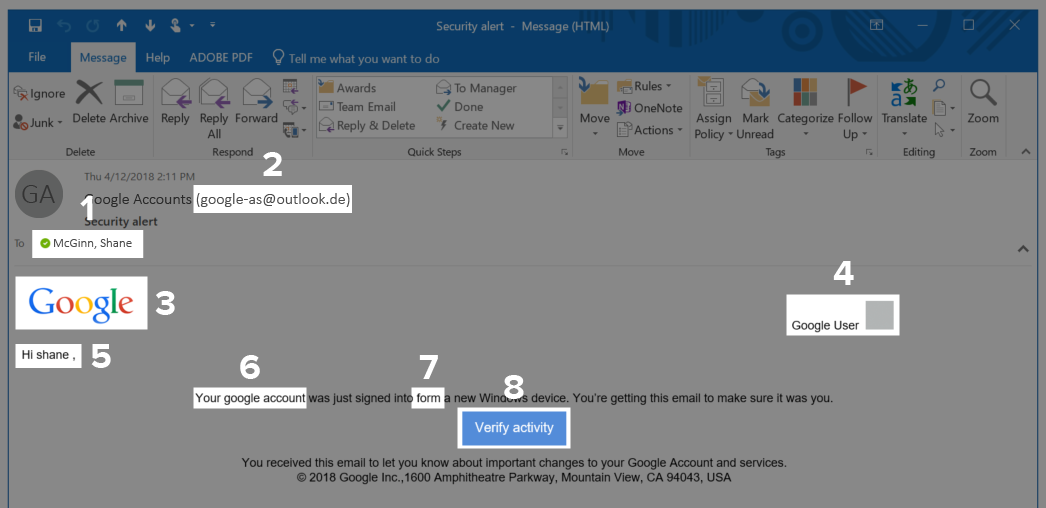
1. Google account email sent to an Outlook address: This can be tricky to recognize, as we often use a single mail client for multiple addresses, but it’s important to think carefully about why a Google email would be directed to your Outlook address. If you don’t have that specific address added to your Google account for recovery purposes, this is almost certainly a bogus email. Be mindful of whether the sender and recipient “make sense” given the content of the email.
2. Bogus sender email: One of the easiest to spot and trademark tells of a phishing attack is an email with a seemingly-legitimate display name but an obviously dubious address. Be suspicious of any company correspondence that comes from an address that is obviously fake or made to look real—you might have to look extra close, but a “0” in place of the letter “O” or a subtle misspelling can trick you. Close, careful reading will help you spot an imposter.
3. An outdated logo: We’re using a very recognizable company in this example, but the same applies to companies you work with frequently. If the logo or assets look like they are outdated or taken from an older version, it’s a red flag. Google hasn’t used this logo for almost three years! A legitimate Google employee is highly unlikely to make such a glaring error.
4, 5. Missing or incomplete information: Notice in this email that the attacker addresses the user by their first name (not capitalized), and a nondescript field in the top right. Attackers want you to trust the minimal amount of detail they give you and fill in the details yourself to make their attack look harmless. In this case, typical Google alerts would include your picture and name rather than a grey box and “Google User.”
6, 7. Dubious spelling: Notice that “Google” isn’t capitalized, and “from” is misspelled. Not all attackers will be this sloppy, but if you see a spelling error in an email claiming to be official, remain circumspect. Sure, typos do occasionally happen, but more likely this is the work of individual attackers, not poor spell-checking.
8. Dangerous links: The link is the ultimate weapon that takes you out of your email client and into dangerous territory. Clicking this button could redirect you to a site designed to perfectly mimic the Google homepage with the intent of capturing your login information, or any number of other methods of attack. It’s essential to always be mindful of links; a quick hover over with your mouse cursor could reveal an obviously bogus, unsecured website or link to a malicious file.
Did you know? In a recent report, Verizon found that 30% of phishing communications are opened by targeted victims and 12% of those users click on the malicious attachment or link. In another report, SANS Institute stated that 95% of all attacks on enterprise networks are the outcome of successful spear phishing. When in doubt, the best way to be certain is to find the information you need on your own instead of following the URL. For our example, you could go straight to google.com, log in to your account, and verify the information in the email knowing that you’re doing so through secure channels.
So how’d you do? Sometimes the signs can be obvious, but smart attackers are constantly evolving their tactics, so fakes aren’t always so easily spotted. If you missed anything we’ve listed in this example, that single flaw could mean the difference between spotting a trap and falling prey to phishing. To help mitigate cybersecurity risks, consider cybersecurity training for your company's employees.
Get the latest in phishing prevention training and cybersecurity consultation from the experts at Align. Speak to an expert today.
Interested in learning more? Download the infographic below to learn about the top techniques used by social engineers.

Email Image Sources: Align




